In my last post, I used the regtime.pl and mactime tools to help determine the potential time a malware infection occurred. In this post, which is very similar to the previous post, I will follow the same steps, however this time I will use the Sleuthkit tools and mactime to analyse the file system changes to determine potential infection time. Normally, you would start with either the registry or the file system mactime, and then move to the alternative based on your findings. However, I thought it would be beneficial to show how the timeline generation and analysis is the same no matter which you start with.
This time using the SANS Forensics SIFT Workstation VM image, I will use the SleuthKits fls and ils commands to produce file system information that can be used by the mactime utility to produce a timeline.
After starting the SIFT workstation I mounted the suspect hard drive to a read-only mount point.
Using the command format of “fls –r –m C: <filepath> > /tmp/fls.log” the file system on the suspect drive was processed for to retrieve any information on allocated or unallocated files in the file system.
The options used were:-
| -m |
mactime output |
| -r |
recursive |
| <filepath> |
/dev/sdc1 – This is the device file for the partition being analysed
|
Using the command format of “ils –m <filepath> > /tmp/ils.log” the filesystem on the suspect drive was processed to retrieve any unallocated inodes on the partition being analysed.
The options used were:-
| -m |
mactime output |
| <filepath> |
/dev/sdc1 – This is the device file for the partition being analysed
|
Once I had the separate output files I then ran “cat” to join them all together. This was done by using the command:
cat <filename> >> /tmp/mactime-body
Then I ran the Sleuthkit mactime program across the mactime body file in 3 ways.
-
- Mactime -b /tmp/mactime-body > /tmp/mactime-body.log
- Mactime -b /tmp/mactime-body -d -m > /tmp/mactime-body.csv
- Mactime -b /tmp/mactime-body -d -m 2009-01-01 > /tmp/mactime-body2009.csv
| -b | format output in mactime body format |
| -d | create a comma delimited file |
| -m | use numeric months and not named (i.e. 01 not Jan) |
| 2009-01-01 | print only timestamps after this date |
The first one will give a full dump in standard Sleuthkit mactime default output. The second one will output a full mactime file in a comma delimited format where each line has its own timestamp. The last one is the same as the second except I am only outputting any information that changed after the 1st Jan 2009.
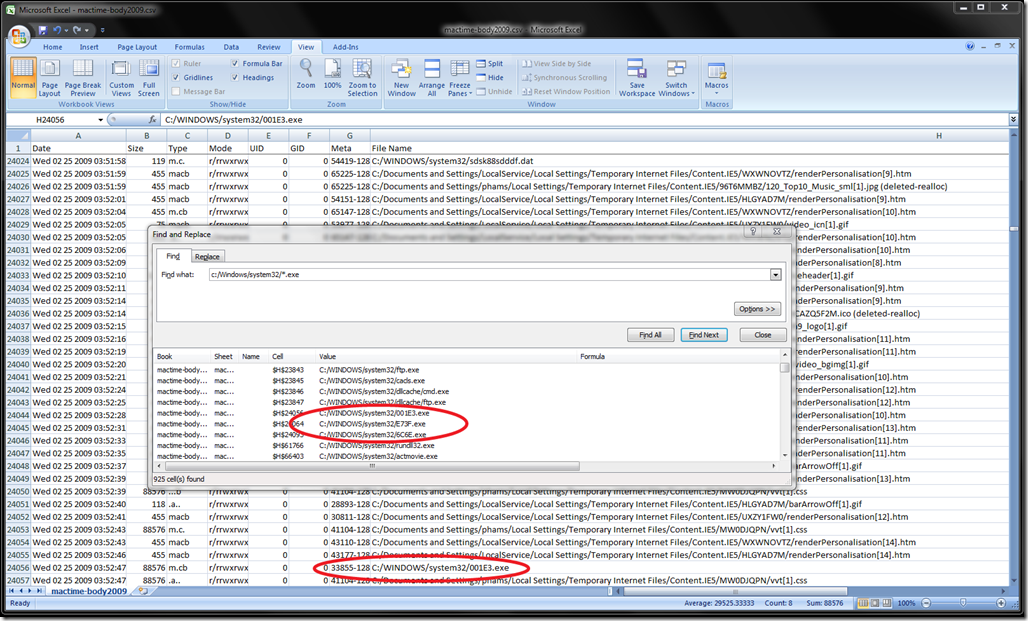
From there I copied the processed mactime files from the SIFT virtual workstation onto a machine with Excel2007 on it. You really want to be using Office2007 to get around the row limit in previous versions of excel. The benefit of using Excel is that it can be quick and easy to sort, search and filter information that may be of interest in the mactime output files. For example, loading up the mactime-body2009.csv file I can do a find all on .exe files that are modified (including created and deleted) in the C:\Windows\system32 directory. The main reason any .exe should be modified here is if there is a Microsoft patch installed. However, since this directory is included normally in the execution search path, malware likes to be dropped in here to avoid execution issues.
Attached is a copy of the the output of the find all command in Excel 2007. When reviewing the timeline we can locate the same time period that was determine in the previous blog as a point in time of interest.